"Tachyon Protocol as a new blockchain protocol is designed to empower online markets and e-commerce platforms"

Hello everyone, welcome back to another edition of Tachyon's technical guide. Here we explore various aspects of Tachyon architecture. We have reviewed the Tachyon Booster UDP (which is the core of the Tachyon ecosystem) and the Tachyon Security Protocol (which ensures that the Tachyon ecosystem remains safe).
In this article we will explain Tachyon Anti-Analysis (TAA), the third level of the Tachyon protocol package. When it comes to decentralized networks, it's easier for hackers to monitor all network communications and attack one individual node through which information is distributed. After the node is compromised, the attacker has the potential to access all data and disrupt communication channels.
TAA is responsible for ensuring that data transmissions occur in such a way that it is nearly impossible for potential hackers to track network communications or access messages sent as a whole. This is achieved through 2 mechanisms - the Simultaneous Multi-trajectory Routing Scheme and the Multi-Relay Forwarding Scheme.
Simultaneous Multi-path Routing Scheme
In concurrent multi-path routing, messages are broken down into smaller data packets and routed to the destination address through several paths simultaneously. This blurs the entire connection route. Packages can arrive at the client's address in any order, where they regroup in the right order to retrieve original information.
To explain this in a little more detail, let's assume that the user sent a message (A). The message will be broken down into IP packets (A1), IP packets (A2) ... IP packets (A5). In each IP (n) packet, Head will form a tree structure where information A is the parent node. The result of Information hash (A) SHA-256 will be used as an IP Packet index to form this tree.
IP packets will be routed through different proxy servers Proxy (S1), Proxy (S2) ... Proxy (S5) until they reach the Tachyon client node. After the client receives all IP packets, he can use the IP packet index to retrieve the original message (A) as a whole.
About
Cryptocurrency like Bitcoin or Altcoin seems to be a good tool for exchanging around the world. Yes, forget some real currencies that are only available in some countries. Along with the development of internet technology, every transaction can be done globally by using it. Interestingly, not only is it more flexible to shop or buy things, it seems that you have to use Cryptocurrency in a smarter way. One of them is to use it as an object of trade and investment. So how?
Of course, first of all, you must join the Cryptocurrency website platform which allows you to carry out sponsorship activities such as trading and investing. This is very difficult, especially for crimes such as fraud which are quite common nowadays. Meanwhile, there are many websites that offer these facilities so you might not know whether they are valid or not. Therefore, you must use the Tachyon Protocol as a new blockchain protocol designed to empower online markets and e-commerce platforms. This is a type of Cryptocurrency platform with simple requirements, easy access and many great features but with a very high level of security to prevent hackers from entering the system. This is even more interesting because suggestions and discussions are available here to support you to be more successful in the future.

Even if an attacker succeeds in compromising one node, he can only get a portion of the information and not the entire message. As the number of nodes in the Tachyon network continues to increase, the difficulty faced by each attacker in intercepting all communication will increase exponentially.
Multi-Relay Forwarding Scheme
The multi-relay forwarding scheme is based on Onion routing, which is a well-known technique used for anonymous communication over computer networks. In this scheme, the data packet is forwarded with some encryption via a short relay, so that no intermediary node can know the forwarding content or routing path. As a result, even if a node in a communication channel is interrupted, the attacker does not have the means to determine the actual communication channel and track the information sent.
Let's see how this scheme works. Suppose node A wants to send a message to node D, with B and C as the intermediate node. A will encrypt the message with public key D and put it in an envelope marked D. However, instead of sending the envelope to D directly, A will encrypt the envelope with public key C and encrypt it as a message to C. After that, A will enter the message this into the envelope marked C, but again, instead of sending it to C, A will encrypt the message with public key B as a message to B.
Finally, A will send this message to B. In its part, B will decrypt the message, take the envelope marked C, and forward it to C. Again, C will decrypt the message and forward the encrypted envelope to D. Finally, D will decrypt the message and reconstruct original message from A.
To know that node A sends a message to node D, the attacker must compromise with node B and node C together. Similar to concurrent multi-path routing, multi-relay forwarding also ensures that taking over one node in the network does not harm the entire communication channel. And the more the number of nodes in the network, the smaller the probability of a successful attack.
With this, we complete our journey to the technical side of Tachyon architecture. But just wait, we have far more alluring content waiting for you guys. Don't forget to check out our whitepaper for more information. Continue to follow our Medium account for further insight into the Tachyon Protocol.
About V SYSTEMS
V SYSTEMS is a general purpose blockchain database for decentralized applications. Led by Chief Architect Sunny King, blockchain V SYSTEMS has implemented its new innovative consensus algorithm - Supernode Proof of Stake (SPoS). V SYSTEMS aims to deliver a decentralized and durable, decentralized cloud database technology, with high finality, performance and the highest resistance to attack by 51%.
About X-VPN
X-VPN is the world's leading VPN service provider on the internet, with 50 million active global users covering 232 countries and regions. X-VPN is one of the 20 largest mobile applications in the world on the Apple App Store and Google Play, and is known as a leading internet brand globally.
The advantage when using VPN on the Tachyon Protocol system
Fast processing speed, easy to use
Tachyon can avoid Sybil attacks and medium attacks, because some organizations can join the VPN network for a short time to monitor
When viewing a hacker intrusion signal. Tachyon will be secured with a very strong two-layer system
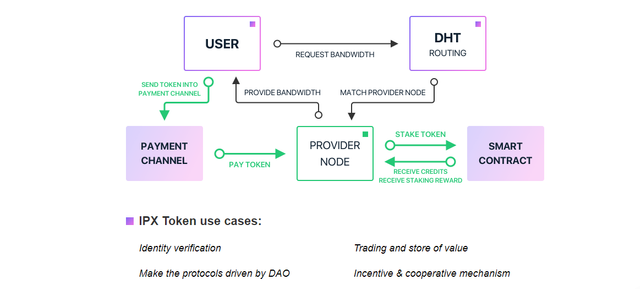
IPX token token
The IPX token is a blockchain token that resides on the V SYSTEMS blockchain network. When you are an IPX holder, you can participate in the Tachyon network. Tokens provide an easy and affordable way to share the backup bandwidth of a node, with the aim of strengthening stability and growth in the network.
The IPX token can be used as the following function:
- Verify identity for the provider's node. This is important for Tachyon Protocol Network security, because without tokens for identity verification, malicious nodes can easily monitor traffic and damage network security.
- Another goal is that the token serves to ensure the network is driven by community participants, and not Tachyon's funding team, which will extend the vitality of the project.
- IPX tokens can be used for trading and storing values. IPX tokens allow the Tachyon market to operate through pre-session locking, instant checkout, and session fee collection.
- As an important part of the incentive and coordination mechanism, IPX tokens are also important for network expansion. Fly the development of the Tachyon ecosystem.
Tachyon Protocol's great partner

Conclude
Projects show that an experienced team, they always work hard to develop projects to stand in the cryptocurrency market. The Tachyon system is increasingly trusted and used throughout the world. In the near future maybe Tachyon will control the entire internet market
Stay connected
Don't forget to follow us on this platform and get notifications. Launch a heated discussion about Tachyon anytime anywhere.
➤ Telegram Group: https://t.me/tachyoneco
➤ Telegram Channel: https://t.me/tachyonprotocol
➤ Twitter : https://twitter.com/tachyon_eco
➤ Medium : https://medium.com/tachyon-protocol
➤ KaKao: https://open.kakao.com/o/gRTetMzb
➤ Reddit: https://www.reddit.com/r/TachyonIPX/
Author ( chaniagho )
Bitcointalk Profile : https://bitcointalk.org/index.php?action=profile;u=2701563
Wallet Address : AR2gAMkd228hCRzcgpfXQPtyFHuVwFBFkzH

Tidak ada komentar: